Introduction
The blog discusses the current business landscape where many companies heavily depend on external vendors for providing essential services. This trend has expanded across multiple sectors, including finance, due to the complexities and interdependencies of modern business operations requiring specialized expertise and resources that might not be readily available or cost-efficient within individual firms. By utilizing third-party service providers, companies can gain benefits like economies of scale, innovation, flexibility, and efficiency.
However, this heightened reliance also introduces new risks, particularly because adversaries tend to target weaker links, often found among third-party suppliers. These vulnerabilities increase as businesses become more dependent upon software and technology acquired through vendors. To mitigate these risks, organizations must carefully manage their third-party ecosystems by understanding their own vendors’ networks and sometimes extending awareness deeper into the supply chain.
The Importance of Third-Party Risk Management
External Collaborators: Concept of Third Parties
Any external entity engaged with your organization constitutes a third party. This encompasses suppliers, manufacturers, service providers, business partners, affiliates, distributors, resellers, agents, and vendors. Given the significance of these external connections in business operations, Third-Party Risk Management stands as an indispensable element within all risk frameworks.
Exploring the Vendor Ecosystem: Third party v/s Fourth party
Understanding your vendor ecosystem and its role in supporting your digital supply chain is crucial. Identifying the providers of digital products and services critical to your company’s operations is essential. Delving deeper into your digital supply chain involves assessing potential risks from various sources:
- Data Breaches and Privacy Concerns: Data flowing through the digital supply chain is vulnerable to breaches, risking sensitive information exposure.
- Supply Chain Interruptions: Disruptions in the supply chain can impact operations, emphasizing the need for resilience.
- Third-Party Vulnerabilities: External vendors’ security weaknesses can pose risks to your organization, necessitating robust risk management practices.
By proactively managing these risks, organizations can safeguard their interconnected ecosystems and maintain operational continuity in the face of evolving digital threats.
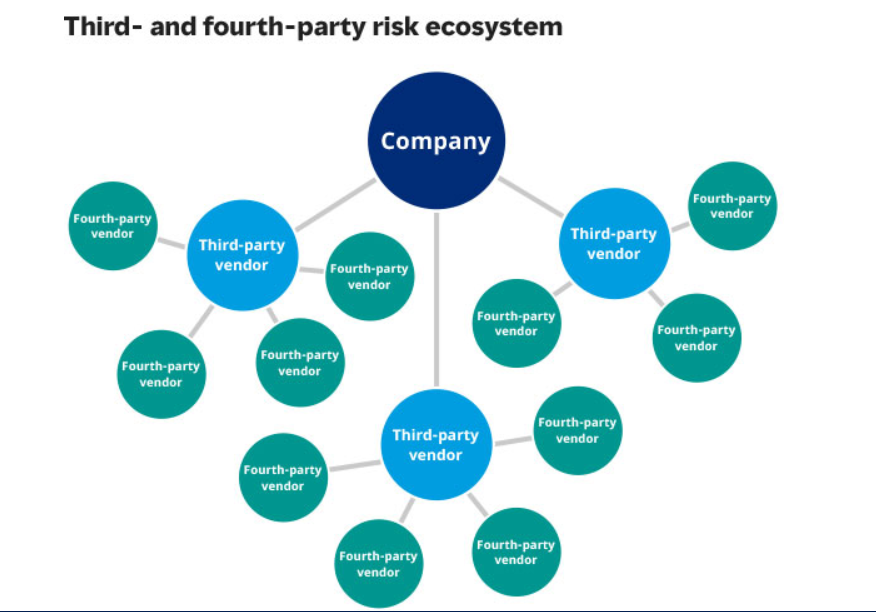
Exploring the Distinction Between Third and Fourth Parties
Third-party vendors, encompassing entities providing products or services directly to your organization for daily operations or on its behalf (e.g., technology vendors and critical suppliers), can introduce risks to all organizations, particularly those with technological connectivity or data access.
Fourth-party vendors, the suppliers of your suppliers, expand the outsourcing network. As companies engage multiple vendors and suppliers, these entities further outsource operations to additional suppliers, amplifying the attack surface and potential vulnerabilities within your ecosystem.
Expanding your vendor ecosystem increases your exposure to risks and vulnerabilities, emphasizing the importance of robust risk management practices to safeguard against potential threats.
Mastering Third-Party Risk Management: Shielding Against Financial Losses, Damaged Reputations, and Regulatory Violations
Third-Party Risk Management (TPRM) entails recognizing, evaluating, and addressing dangers arising from engaging third parties for core business processes. Such hazards may lead to financial losses, tarnished reputations, and noncompliance with regulations.
This discipline reinforces the significance of technology risk management, risk insurance, and their indispensable roles in shielding organizations from perils. Although risk insurance cannot protect against reputational harm, understanding its limitations helps businesses prepare more effectively for potential crises.
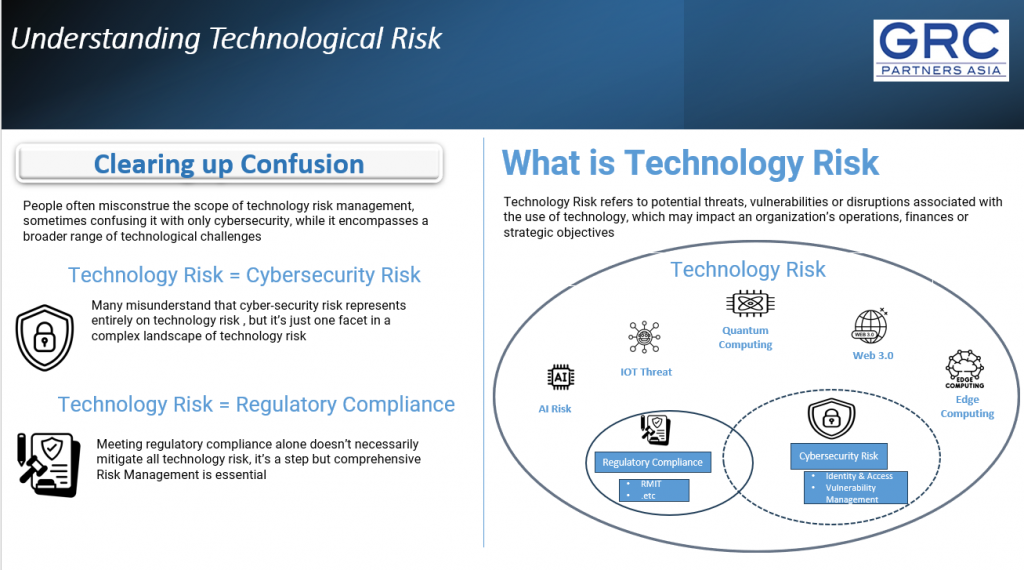
Below is a simplified representation illustrating the central concepts of Technology Risk Management:
Third parties increase the complexity of your information security for several reasons:
- Third parties often operate independently, with limited visibility into their security measures. While some vendors uphold strong security standards and risk management protocols, others may fall short.
- Every third party represents a potential entry point for cyber threats and data breaches. Exploiting a security flaw in a vendor could lead to unauthorized access to your organization. The greater the number of vendors you engage with, the broader your attack surface becomes.
Key Takeaway
Given the expanding landscape of third-party dependencies, organizations must embrace TPRM as a fundamental aspect of their broader risk management strategy. Failure to do so leaves firms exposed to potentially devastating consequences, ranging from crippling financial losses to irreparable reputational damage.
The Difference between TPRM and VRM
Although vendor risk management (VRM) and third-party risk management (TPRM) are often confused or used interchangeably, it’s important to recognize that they’re distinct concepts.
What is VRM?
VRM refers to the process that organizations use to ensure that third-party products and services don’t lead to negative financial, reputational, regulatory, operational, and strategic consequences. VRM is all about vetting partners, suppliers, and vendors to make sure they meet certain conditions.
What is TPRM?
TPRM extends beyond vendors to encompass diverse third parties, such as partners, governments, franchisees, and charitable organizations. These entities may handle sensitive company data without full control over user access or audibility.
Key Takeaway
TPRM often starts with VRM; it’s the foundation on which TPRM is built. Organizations will begin with a VRM program, and as they grow and mature, they’ll identify a need to address the specific and frequently disparate risks that a growing list of third parties present.
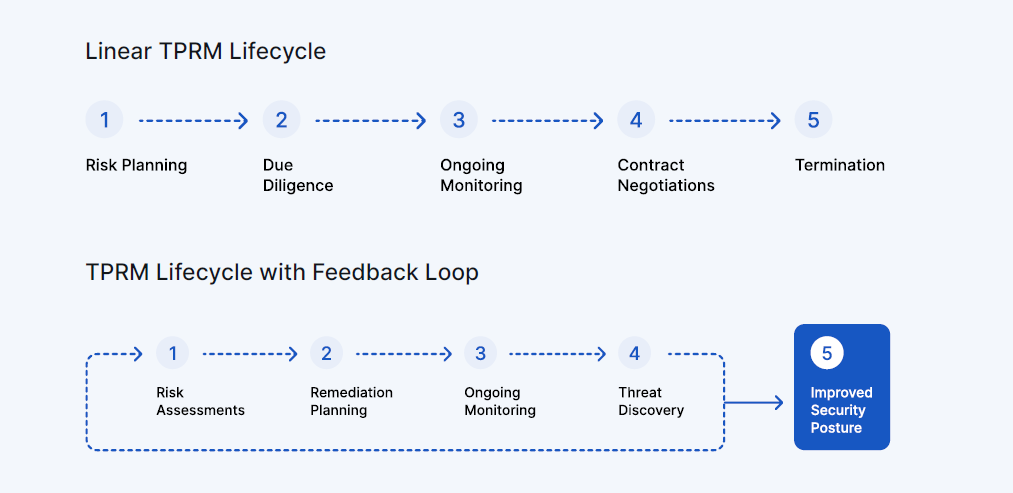
The Third-Party Risk Management Lifecycle
The Third-Party Risk Management Lifecycle involves a series of stages from pre-contract risk assessment to post-contract monitoring, ensuring effective risk identification and mitigation throughout the relationship with third parties.
Ongoing management of evolving third-party security risks is possible with the following 5-stage TPRM lifecycle.
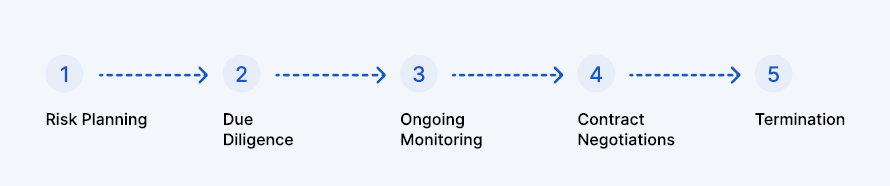
1. Risk Planning
- Evaluate your third-party risk appetite – Based on acceptable inherent and residual risks. This risk appetite will be modified after onboarding when applicable regulatory and compliance requirements are considered in greater detail. After such considerations, final alignment with your risk threshold could be measured with resultant residual risk ratings.
- Evaluate and determine how to best tier your vendors – This is a crucial step that is often overlooked. Tiering vendors based on the information they will have access to, the product/service they are providing, or their regulatory/compliance requirements will help you determine the level of risk monitoring and due diligence each vendor requires. Intelligent vendor tiering will also help you track the reassessment (or recertification) schedules of each vendor grouping.
2. Due Diligence
- Determine critical due diligence questions – Multiple data sources should be referenced when designing these questionnaires, including previous quarterly risk reports, internal audit reports, industry standards/regulations, and previously completed risk assessments.
- Evaluate each vendor’s inherent risk score – Before considering any third-party security controls that will be required in a partnership arrangement, a security risk baseline should be established through a simple risk assessment or questionnaire. This will help you determine the level of controls needed to keep each vendor’s risk exposure within your risk appetite limits.
- Confirm the validity of due diligence processes – All due diligence risk assessments should be confirmed with a security rating scoring system based on multiple attack vectors.
3. Contract Negotiations
- Establish security standards in vendor contracts – This will depend on the jurisdiction you operate in.
- Consider relevant data breach notification periods – Depending on your region and the regulations that apply to your organization, you may have minimal third-party vendor breach notification timeframes your vendors should agree to.
- Complete internal security breach clauses – Include a contract stipulation to report any minimal internal security incidents not classified as public data breaches (it is better to be overinformed about the security posture of your vendors than underinformed). These events could be communicated in a General Incident Report.
- Consider adding a ‘Right to Audit’ clause in vendor contracts – This will give you the right to review each vendor’s internal security processes, audits, self-assessments, and controls.
- Review stipulated SLAs – To ensure the standards meet your business and compliance requirements.
- Seek TPRM platform onboarding approval – Confirm the vendor’s approval of being onboarded onto your company’s TPRM platform.
- Segregate each TPRM project – Designate an internal primary business owner of each TPRM relationship.
4. Ongoing Monitoring
- Implement continuous attack surface monitoring – Implement systems that track the performance and status of all third-party security controls that are in place.
- Establish internal monitoring triggers – Monitoring systems triggered during critical security events, such as weakening security postures and deviations from regulatory compliance standards.
- Implement service level agreements compliance tracking – Track and assess alignment with stipulated service standards.
- Follow a reassessment schedule – performing routine reassessments of all current vendors based on internal policy and regulatory requirements.
- Account for new risk exposures – Following strategic direction changes or any changes to digital products and services, security postures should be reevaluated to detect new risk exposures.
5. Termination
- Revise user access list after offboarding and contract termination – Revoke all data access and perform a final review of security policy and regulatory standard compliance.
- Implement data deletion processes – In certain regions, it is mandatory to delete data and provide evidence of this process. Please review the regulations applicable to your jurisdiction to verify the necessity of data deletion and obtaining a certificate confirming the deletion.
Importance of Integrated Feedback Loops in Third-Party Risk Management
To enhance responsiveness to shifting third-party risks, a feedback mechanism is incorporated within the TPRM lifecycle, guaranteeing that corrective actions consistently target emerging threats.
Key Takeaway
Incorporating a feedback loop establishes an iterative framework that can flexibly adjust to evolving risk appetites, security policies, regulatory compliance standards, and business relationships. The revised TPRM lifecycle model can also account for unique third-party risks that extend beyond cybersecurity, commonly referred to as special categories of risk.
Special categories (or non-traditional categories) of risk include entities that have the potential of becoming third-party breach attack vectors despite not commonly being targeted by cybercriminals.
The management of special third-party risks is especially an important capability for financial institutions.
Common examples of special third-party risk categories are listed below:
- Insurance agents
- Reinsurers
- Brokers
- Third-party administrators
- Powers of attorney
- Indirect lenders
Third-Party Risk Management doesn’t have a destination. It’s an ongoing process of Learning and adjusting to each vendor’s emerging security risks.
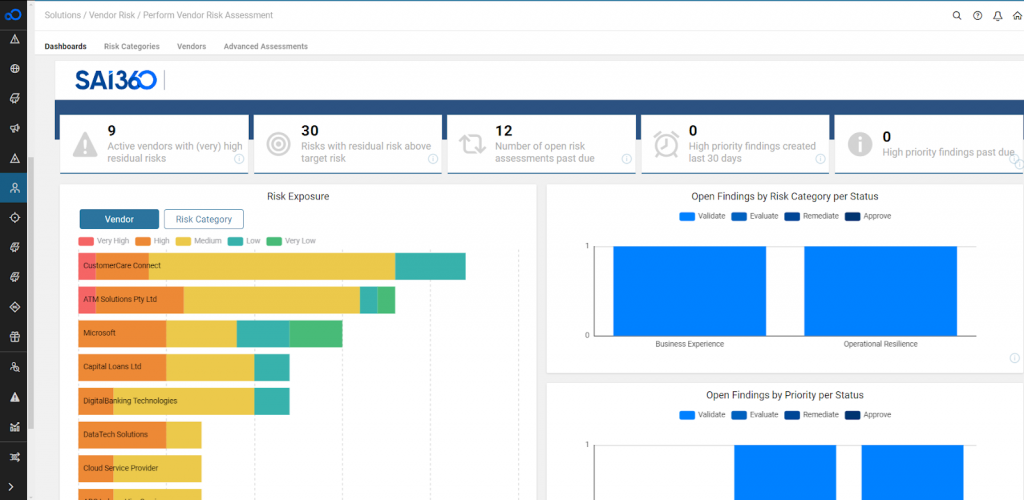
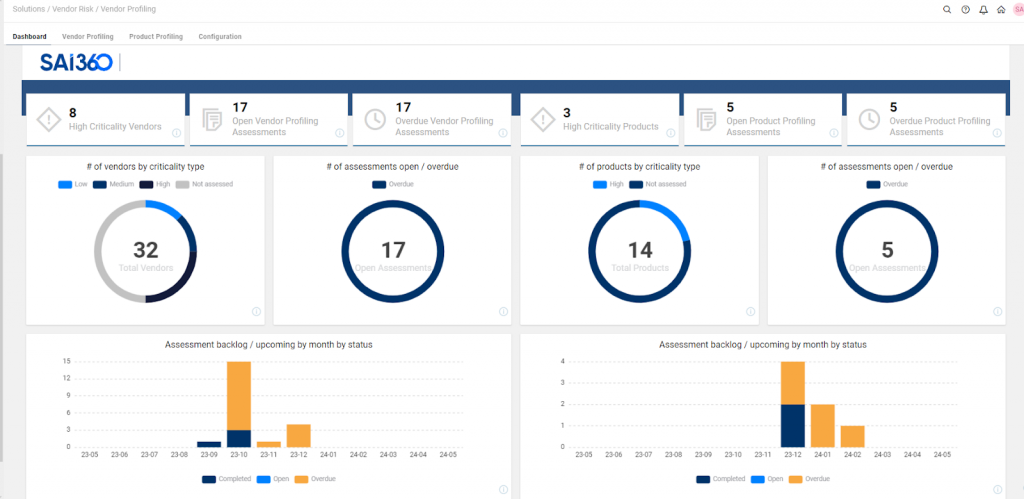
How SAI360 helps?
The SAI360 Third-Party & Vendor Risk helps organizations to:
- Scale up their coverage of third parties.
- Facilitate collaboration to maintain healthy business relationships.
- Get deeper insight into their extended enterprise through due diligence and security rating services.
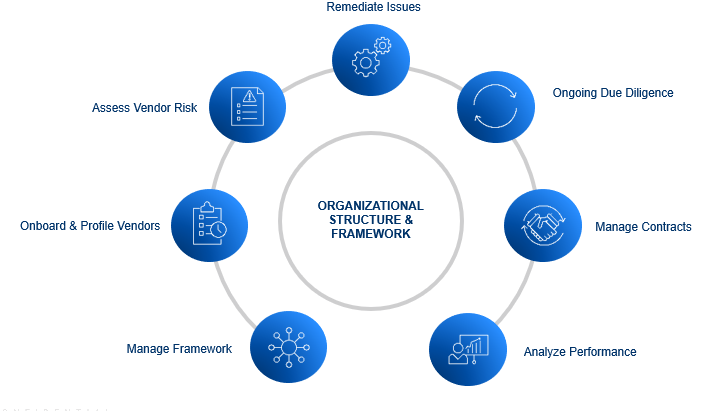
Key Capabilities
The figure below shows an overview of the key steps within the TPRM process and the core functionality supported by the module.
Out-of-the-box Features
- An industry-leading questionnaire library based on popular regulations.
- Automated due diligence with SecurityScorecard, WorldCheck, Argos Risk, BitSight, RiskRecon and more
- A custom questionnaire builder for highly targeted risk evaluations.
- A complete third-party risk assessment workflow for seamless risk remediation.
- An industry-leading security rating feature offering instant, accurate insights into vendor security postures.
- Advanced Integration and data analytics.